Data Security by Process Design: The Next Step for IT and IP Protection
I was sitting next to a HoneyBadger Bitcoin employee on a plane a few months ago – he was moving forward their kiosk deployment across Canada and I was half asleep heading home from Seattle – and finally got an answer to a question I’d been wondering for a long time: How do those ‘in the know’ secure their wallet numbers and passwords when everything is hackable?
His answer: pen, paper, safety deposit box. I’m not sure what I was expecting, but that certainly wasn’t it.

^ Yup. Still a thing. (Getty Images)
That message, in context with last week’s news that QuadrigaCX has now forever lost access to ‘cold wallets’ worth over $160 million – and the record $865 million dollars worth of coins stolen from exchanges around the world in 2018 alone, now makes a little more sense.
Pen, paper, safety deposit box indeed.
Electronic thieves have innovated. Clever phishing emails, fake websites and spoofed email addresses (many of you have seen them I’m sure) have taken over the ‘ prince’ emails. Faked wiring instructions from colleagues, fraudulent CRA phone calls and mysterious banking password verifications all seek to get through the IT infrastructure we’ve set up to protect ourselves with verified credentials. You don’t need a hack when you can convince targets to bring you behind the ‘silicon’ curtain – or avoid it altogether. Even blockchain security can’t prevent a compromised user from making changes to secure data.
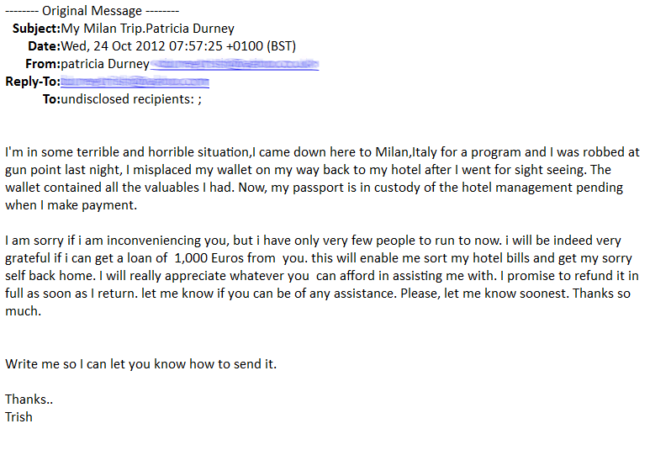
^ A ‘Londoning’ Scam – One of the originals. When in doubt, call the hotel directly. Their confusion will be real. That, and your friend is really back in town but just doesn’t want to listen to your story about your dog. That happens.
Unlike an IT hack – a failure of your infrastructure to withstand attack – we are countering a new and different threat: a digital version of the failure of checks and balances that plague many businesses. Growth – especially in small, founder-led businesses – doesn’t often permit the vigilance of enforcement required to prevent financial ‘leakages’ (to use my colleague Salima’s favorite term). Founders need to sell, sell and sell again. Even with expense trackers like Expensify and small business back-office apps like (the rather brilliant, Edmonton-based Jobber), there remains gaps in our ability to provide the requisite checks and balances that will keep our money safe from phantom bills or instructions.

^ We <3 you, M-Files
Our solution – the best solution (though we may be biased) – is to fill the gap between costs and approvals by cementing your checks and balances digitally. A strong document management system (we use MFiles – it does this seamlessly) can build processes that manage file interactions – necessitating approvals, ensuring completeness, and protect against versioning errors – that mirror the numerous processes you already use to operate your business. We will also evaluate your processes with you to ensure that those that we are recreating accomplish the security tasks they are meant to.
That said, with or without us, I would implore you to protect your critical processes. Create a strict, two-stage process – both verbal and electronic – on how wire transfers, cheques over a certain amount, payment orders and confirmations, how users’ passwords get changed and updated and the digital permissions required for your employees access secure data. Ensure that passwords are changed at the very least biannually (the more the better, but people absolutely hate this I recognize). And, most importantly, keep a data trail – in some way – of these processes. The more automated and unbiased the better.